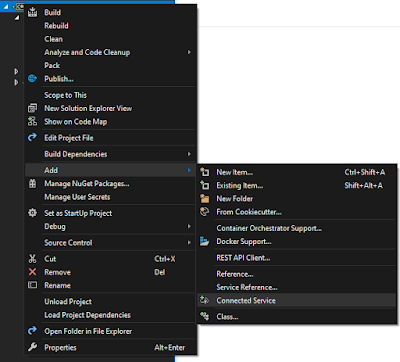
This should bring up a tabbed window to add Connected Services. We're interested in the WCF:
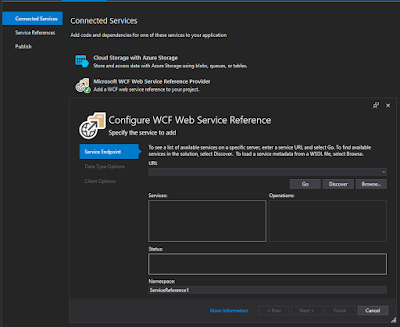
Enter the URI for the SOAP interface of interest and press the Go button. If all went well, the available service(s) should be listed. Enter a namespace and click next to see additional options. For more information see the documentation: Use the WCF Web Service Reference Provider Tool.
For more details on WCF, see the github dotnet wcf repo .
This abstraction of course has a flip side: The actual data transferred is buried deep in the internals so any single-step debugging cannot "see" the raw HTML/raw XML payload. This is where Fiddler comes in to help. (yes, if you've not used Fiddler for some time, it was bought by Telerik, which was bought by Progress).
Before getting started, the netsh command will be used. It is probably a good idea to see how it is currently configured before making changes. To see the current setting, use:
netsh winhttp dumpThe default typically looks like this:
# -----------------------------------------
# WinHTTP Proxy Configuration
# -----------------------------------------
pushd winhttp
reset proxy
popd
# End of WinHTTP Proxy Configuration
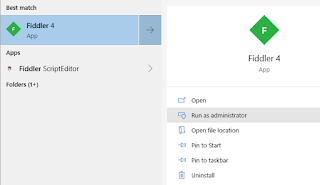
To allow Fiddler to see the packets it needs to run in "Administrative" mode in Windows. Either right-click on the icon and select "Run as Administrator" or after searching for the app, select from the start menu:
We'll need to set a proxy to ensure all http transfers pass through Fiddler. Otherwise it just sits there idle. So yes, the command prompt needs to be running as administrator here, too. This is the command to setup the proxy:
netsh winhttp set proxy 127.0.0.1:8888
When done, return to default:
netsh winhttp reset proxy
If you don't return things to default, web browsers, Outlook, and potentially other things will misbehave, particularly when existing Fiddler. A reboot also restores the proper netsh default state.
A few notes on Fiddler:
-
The `Decode` feature only decodes moving forward. If you see gzip-encoded payload, pressing the button will not decode existing captures.
-
Only newly seen request/responses will be decoded. Press F12 or File - Capture Traffic to being sniffing. A checkbox means packet sniffing is active.
- Data is viewed under the Inspectors tab. I personally prefer the XML view.
This was all related to the WCF GitHub Issue 4071 that I opened up for some problems I encountered when serializing a SOAP response in a dotnet core command line app.
Copyright (c) gojimmypi all rights reserved. Blogger Image Move Cleaned: 5/3/2021 1:35:54 PM