Hackaday Supercon is back!! Here’s a little Badge SAO idea: Wireless SSH Access!

I’ll have a little giveaway this time! I had no idea what to expect at my first Hackaday in 2019. I hadn’t been to any sort of conference in years, and what Supercon is… well, it is not like any conference I had ever attended.
What was really great was the kindness and generosity of all those folks there. One of the first people I met was @mithro who gave my a pair of fomu. There was also @ZxSpectROM that ensured I had a RC2014 board. But me, I just showed up with a ticket in hand. There were many others that were kind and generous.
So this year, I’ve remedied that! First, I’ve made my first ever stickers:

Next, I thought it would be good to have some badge accessories. So I bought some USB-TTY adapters and even some ESP32-WROOM-32 dev boards to give away.

As much as I would have liked, I didn’t have a personal budget for everyone at Supercon… but for the people I meet, and for some people that have been inspirational and helpful on twitter, I have some giveaways, too.

I thought some things that would be a good companion to this year’s badge would be some ESP32 dev boards to go along with my challenge! So in some of the envelops there will be an ESP32-WROOM32 dev board, that should work perfectly with my SSH to UART software.
Although I have the SSH to UART project working, getting something implemented on the 4-bit Badge Processor… well, that’s the challenge!.
In other envelopes, there will be a USB-TTY Serial adapter. Given the primitive nature of the badge, it may be quite interesting enough just to get the UART talking, let alone connecting the SSH server.
I’ll also have some wolfSSL swag to give away. I have a part time gig with them; of course my SSH to UART server is of course based on their wolfSSH library.
Pre-show, there’s seemed to be a bit of discrepancy between the 4-pin SAO connector shown on the Badge Announcement Page and the link to the 6-pin Version mentioned there.
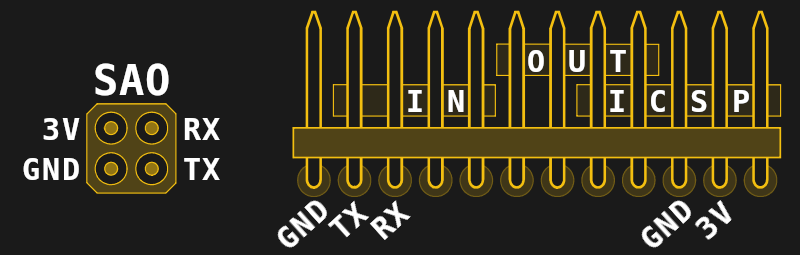
Here’s the 4-pin SAO pinout that I believe will be on the badge:
Here’s the 6-pin SAO pinout that’s referenced:
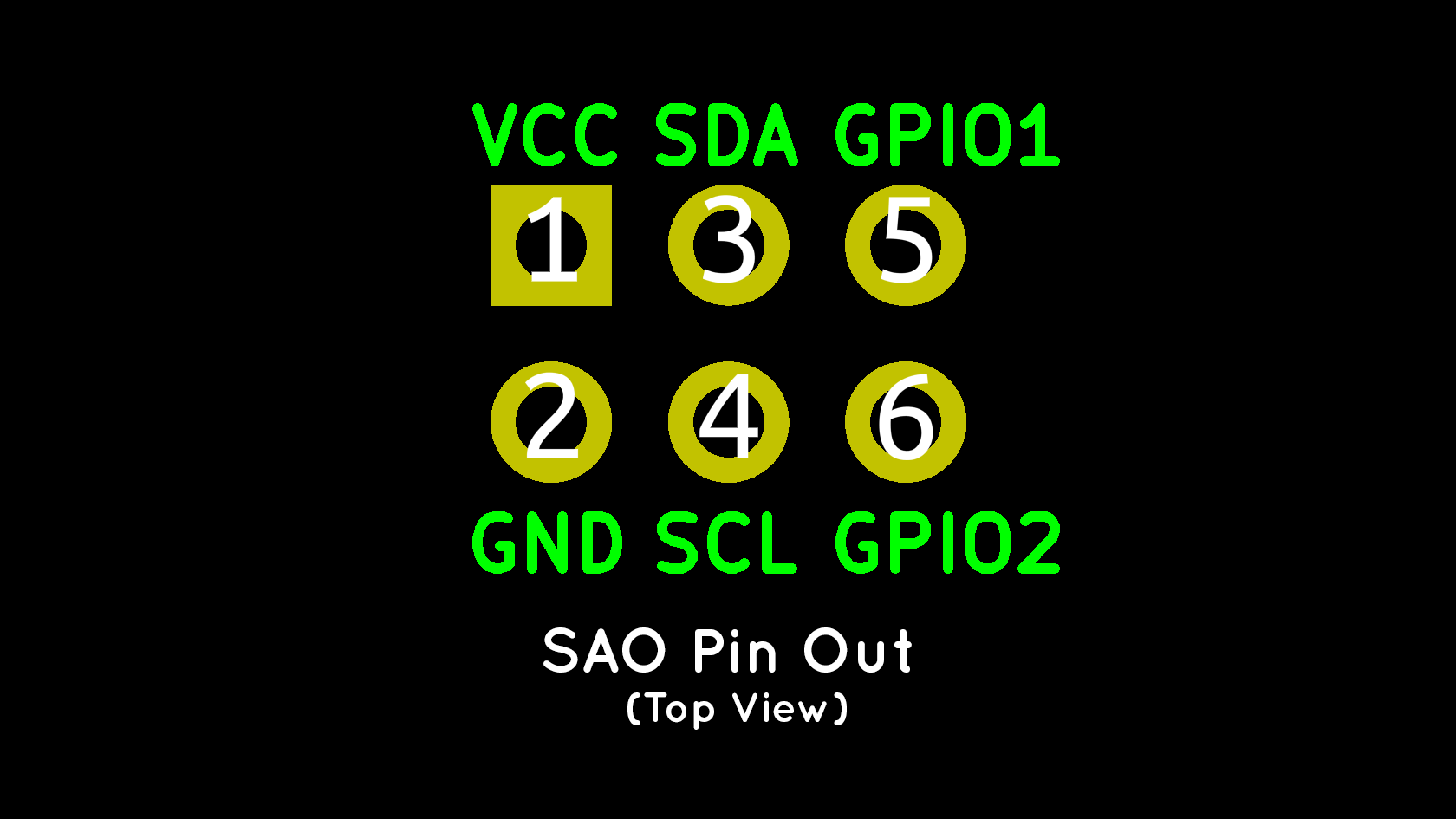
Whichever connector is used, we simply need either the Tx and Rx on the 4-pin or the GPIO1 and GPIO2` on the 6-pin connector.
Don’t forget to connect the ground pin!
Of course, if you want the ultimate ESP8266 Badge SAO, check out the custom board by nschurando. Here’s a link to the schematic.
Watch out though as the pins RX and TX on the 4-pin SOA connector of this year’s badge are mapped to non 5V-tolerant GPIOs of the PIC. So they’ll effectively be limited to VDD+0.3V. And with the 2x1.5V alkaline batteries ever so slightly discharged you’re already at risk of damaging the badge when interfacing it with 3.3V logic.
See the PIC24FJ256GA704-I/PT
To get started - if you want to go the lazy route, you could go with my original development that has a (stale) copy of the wolfSSL and wolfSSH libraries already installed as local project components.
That’s of course not the best route, as there have been several releases in the many months since my repo was last updated. See the setup for wolfSSL and wolfSSH to properly install the latest versions.
Note that my SSH-to-UART project does not use the Espressif esp-tls layer SSH.
Thanks @LinuxJedi that pointed out only RSA is implemented at this time. So if you have your SSH shell locked down, you may need to do:
-o"PubkeyAcceptedAlgorithms +ssh-rsa"
-o"HostkeyAlgorithms +ssh-rsa"
Now, getting even a UART to echo characters with a bare-metal, 4-bit processor is not an easy task. In fact, I learned that the Hackaday Discord chat that the UART is not even an example.
But then that’s the point of a challenge. No fun if it’s too easy.
(this blog page is still a work in progress)
See prior blogs:




